You can never be too secure when it comes to your computer. Be it for family purposes, security, or ensuring that your financial records aren’t messed with. Taking that extra step for protection is a smart move. Almost everything, barring human interaction, can be done on the PC. Programs are streamlined and connected, and the same can be said for social networks and online financial institutions. This is why it is so important to keep track of the many accounts you may have, and to protect your PC from unknown users. At the same time, you can also use this to keep track of the activities of your children, and help protect them from less than legitimate websites. So for this purpose, here are the top 10 key logging software programs you can exploit. Take note; most of these programs are free, but there are also countless replicate programs so be cautious when downloading a program.
10. Spector Pro

Among all the programs that are going to be mentioned, this is probably the priciest of the bunch. Spector has a $100 price tag attached to it, and will no doubt rip a hole in your wallet. However, upon installation, it does implement the features that it boasts. All it needs are specifics and which profile it needs to monitor. However, it lacks the ability to monitor keystrokes remotely.
9. ReFog
ReFog is a couple of notches better the Spector. It boasts all the same features, but at the same time, can be viewed remotely. It is efficient in watching key strokes along with any activity that you deem out of bounds. However, it lacks the ability to block specific URLs, and will at times simple observe the actions of the user. This mitigates your control quite a bit which diminishes the value of this program. ReFog is also much cheaper than Spector Pro.
8. Stealth Keylogger
The name of the program should already give away its prime purpose. This program is designed to be as under-the-radar as possible. It runs quietly in the background, and has low resource consumption. This effectively means that it won’t get in the way of any activities the user might be taking part in. remote monitoring also factors in heavily as you can be on the go while being up to date with your computer’s activities. The recurring problem with this program is that it has a weak URL interception feature that might allow for a websites getting past the net.
7. Elite KeyLogger
Yet another security program that can really benefit the household, Elite KeyLogger has a few key features that surely nip many problems right in the bud. It can store countless URLs and blocks them quickly and efficiently. It keeps tracks of keystrokes with much accuracy, which is the key in keeping a lot of your accounts secure. The problem with this program is that it doesn’t log activity, and cannot monitor chats between computers or social networks.
6. StaffCop Standard

StaffCop has strength, which is also, peculiarly, its weakness. The program has a ton of features beyond keylogging, but it also keep an accurate and detailed report of keystrokes and sites visited. However, it is evident that the program is mostly aimed at offices and businesses. It doesn’t have much in the way of parental control, but it can keep track of many computers at the same time. It can also be locked, only usable by the main computer when the program has been compromised in other stations.
5. KidLogger

For parents that wish to protect their kids from lewd materials, or are looking for a form of punishment that works online, then KidLogger is a program that is aimed directly at that purpose. It keeps track of forums and websites that are otherwise subject to less than reputable popularity. At the same time, it also keeps track of the many chat boxes and logs them right into a file that can be viewed later on. While it can’t protect against some negative elements, it does its job well. It’s also a freeware program, so check it out for a quick test.
4. Home KeyLogger
For people that don’t have the highest tier PCs, but still need a program that can run on an older system, Home KeyLogger answers that need. Boasting the ability to log countless user names and passwords, it eats almost no resources from your PC. The program, however, has limited features but with the right strategy, can be used to cover a lot of websites and programs, which hold a lot of your personal information.
3. SpyTech Spy Agent Stealth Edition
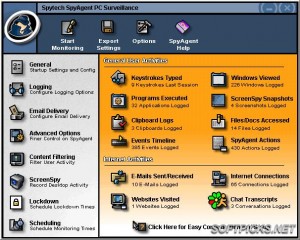
Though the program is pricey, Spytech is still one of the best program for keylogging and security currently on the market today. Along with the massive $80 dollar tag, it also has a whole slew of features and the ability to remotely inform you of any activity that takes place on your PC. It can also block many URLs at lightning fast speeds, which is important for people that need to protect their personal information.
2. Revealer KeyLogger
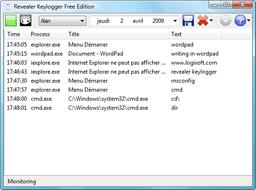
This program is a freeware, which makes it amazing. Sure, it does not have the whole suite of programs and features that paid programs may have, but at the end of it, Revealer does its job efficiently. It captures all keystrokes with speed and accuracy. It tracks programs that were opened, files that were viewed, and websites that have been accessed, and logs all this information with the installer or the administrator. It runs quietly in the background as it does all this, while remaining anonymous to every other user on the PC.
1. Actual KeyLogger
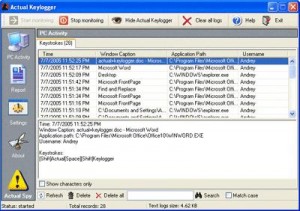
Actual KeyLogger is the best program for the purpose of tracking and security. This is because it basically runs in stealth mode all the time and records every piece of information in the form of HTML or in a Notepad file. It also arranges this information in such a way that it is easy to understand the path of progression between actions. The best part is, the program is only visible to the original installer, and cannot be accessed or even located by those that don’t know that it has been installed.
April 26, 2013 12:49 pm
Thanks for helpful information, as for me I prefer to use Protemac Keybag ( protemac.com )